
Firstly i am going to introduce the term havij :)
Havij is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page.
It can take advantage of a vulnerable web application. By using this software user can perform back-end database fingerprint, retrieve DBMS users and password hashes, dump tables and columns, fetching data from the database, running SQL statements and even accessing the underlying file system and executing commands on the operating system.
The power of Havij that makes it different from similar tools is its injection methods. The success rate is more than 95% at injecting vulnerable targets using Havij.
The user friendly GUI (Graphical User Interface) of Havij and automated settings and detections makes it easy to use for everyone even amateur users.
First Find a sqli infected site .Now here i found a vulernable site
Now Let's start
Open havij and copy and paste infected link as shown in figure
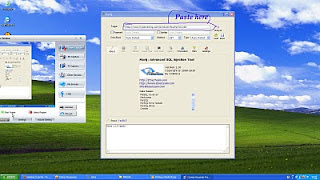
Now click in the "Analyze"
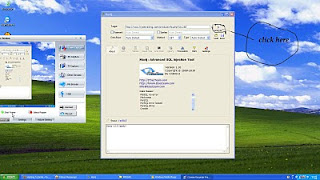
Then It shows some messages there....Be alert on it and be show patience for sometime to find it's vulernable and type of injection and if db server is mysql and it will find database name.Then after get it's database is name like xxxx_xxxx
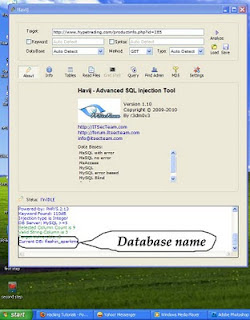
Then Move to another operation to find tables by clicking "tables" as figure shown.Now click "Get tables" Then wait some time if needed
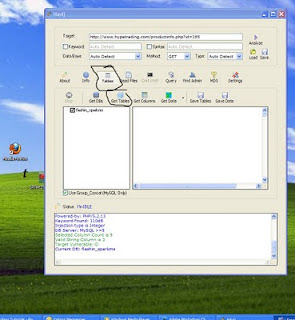
After founded the tables ,you can see there will be "users" Put mark on it and click in the " get columns " tab as shown in figure
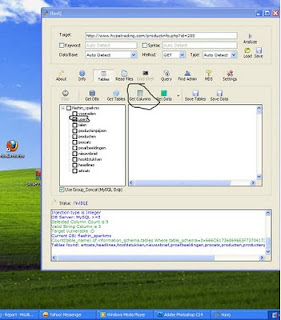
In that Just put mark username and password and click "Get data"
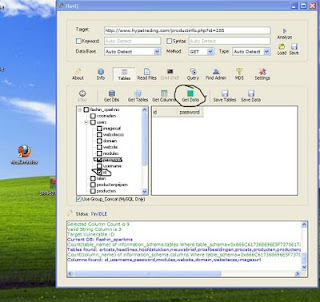
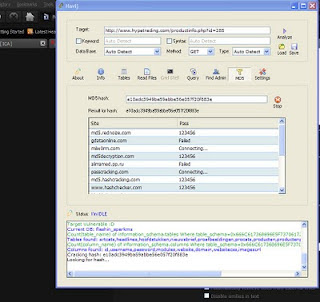
Bingo Got now id and pass that may be admin...
The pass will get as md5 you can crack it also using this tool as shown in figure...
Having problem?? Mention them in your comments. We will help you will definetly solve them.







0 comments